- Home
- Architecture
PRISMACLOUD Architecture
In order to tackle and organize the complexity involved with the construction of cryptographically secured services, we introduce a conceptual model denoted as the PRISMACLOUD architecture, which is organized in 4 tiers (cf. Figure 1). These layers of abstraction help to specify and analyze security properties on different levels; they also define connection points between the different disciplines involved in the creation of secure and privacy preserving cloud services: cryptographers, software engineers/developers and cloud service architects. On the uppermost (i) Application layer are the end user applications. Applications use the cloud services of the (ii) Services layer to achieve the desired security functionalities. The cloud services specified there are a representative selection of possible services that can be built from the tools organized in the (iii) Tools layer. In particular, they represent a way to deliver the tools to service developers and cloud architects in an accessible and scalable way. Together the tools constitute the PRISMACLOUD toolbox. Tools encapsulate the needed cryptographic primitives and protocols from the (iv) Primitives layer, which is the lowest layer of the PRISMACLOUD architecture.
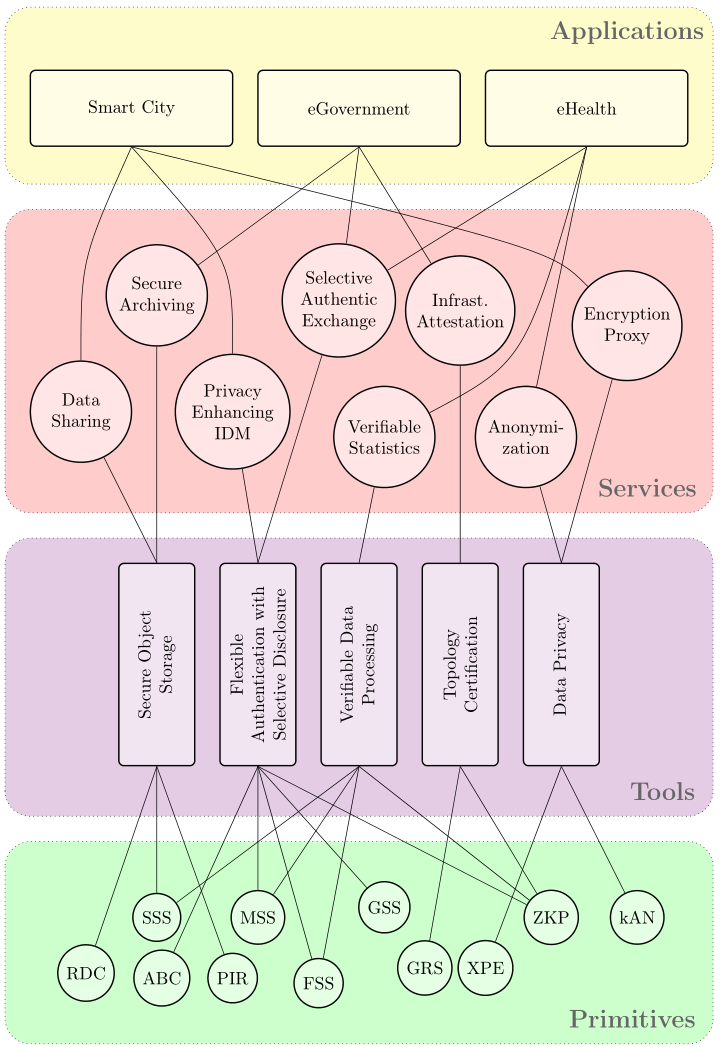
| Figure 1: The PRISMACLOUD Architecture. (Primitives abbreviations: RDC: Remote Data Checking; SSS: Secret Sharing Schemes; ABC: Attribute-Based Credentials; PIR: Private Information Retrieval; MSS: Malleable Signature Schemes; FSS: Functional Signature Schemes; GSS: Group Signature Schemes; GRS: Graph Signature Schemes; XPE: Format- and Order-Preserving Encryption; ZKP: Zero-Knowledge Proofs; kAN: k-Anonymity) |
Instead of directly integrating cryptography into applications or services the PRISMACLOUD architecture introduces an additional level of abstraction: The tool layer. A tool represents a basic functionality and a set of requirements it can fulfil. A tool can therefore be regarded as an abstract concept which could be realized as a piece of software, e.g., a library, which is composed of various primitives which can be parametrized in various different ways. From the tools of the toolbox, the services of the next layer can be built. A service can therefore be seen as a customization of a particular tool for one specific application. It is a way to deliver the tool to system and application developers, the users of the tools, in a preconfigured and accessible way. They will be able to integrate the services without deeper understanding of tools and primitives and ideally without even being an IT security expert. A service provides a full implementation of all the required features as well as concrete interfaces in the form of an application programming interface (API), suitable to be deployed as a cloud service. In PRISMACLOUD we have chosen to specify a selection of services which we will develop during the project and which are suitable for showcasing the suitability of the chosen primitives and the tools constructed from them within the selected use cases. The use cases also provide a way to validate the new concept in real world applications.
With this architecture we encapsulate the cryptographic knowledge needed on the lower layer inside the tools and their correct usage inside services. Building the tools requires in-depth cryptographic and software development knowledge. However, once built they can be used by cloud service designers to build cryptographically secure and privacy preserving cloud services. These cloud services are then exposed to application developers who can combine them with other technologies and services into the real end-user applications.
Additionally to the discussed advantages, the PRISMACLOUD architecture further facilitates exploitation of project results. Each layer provides a dedicated project outcome with a specific exploitation path. Research progress on the layer of primitives leads to scientific progress and typically associated exploitation. Tool developers will be able to commercialize software developments and intellectual property rights. Services developers are able to transform the project results in very short term into products. Their services will be almost ready for deployment in production environments of cloud providers, hence, they will be accessible to a broader community relatively soon after the project’s end. The project also features a specific standardization activity to disseminate the tools’ specifications into standards to support further adoption.
What we termed the PRISMACLOUD architecture can be seen as a recipe to bring cryptographic primitives and protocols into cloud services that empower cloud users to build more secure and more privacy-preserving applications. In its core we encapsulate the cryptographic knowledge in specific tools and offer basic but cryptographically enhanced functionality for cloud services. In PRISMACLOUD we will harvest the consortium members’ cryptographic and software development knowledge to build the tool box and the services. The resulting PRISMACLOUD services hide and abstract away from the core cryptographic implementations and can then be taken by cloud service designers. On this level of cloud services, the PRISMACLOUD services will show how to provision (and potentially market) services with cryptographically increased security and privacy.

