- Home
- Secure Cloud Services
PRISMACLOUD Services
In PRISMACLOUD a protfolio of novel security and/or privacy enhanced services has been developed. Based on the PRISMACLOUD Architecture a service can be seen as customization of one particular cryptographic tool (or several particular tools) PRISMACLOUD toolbox for one specific from the application scenario. It provides a set of features which has been identified as particularly useful for a broader class of applications scenarios the service is targeting.
Secure Archiving Service (SAaaS)
The PRISMACLOUD secure archiving service is a generic infrastructure service which can easily be integrated into cloud based backup scenarios while providing a demonstrable higher level of data privacy and availability than current cloud-based archiving solutions. The delivery model for this service is IaaS.
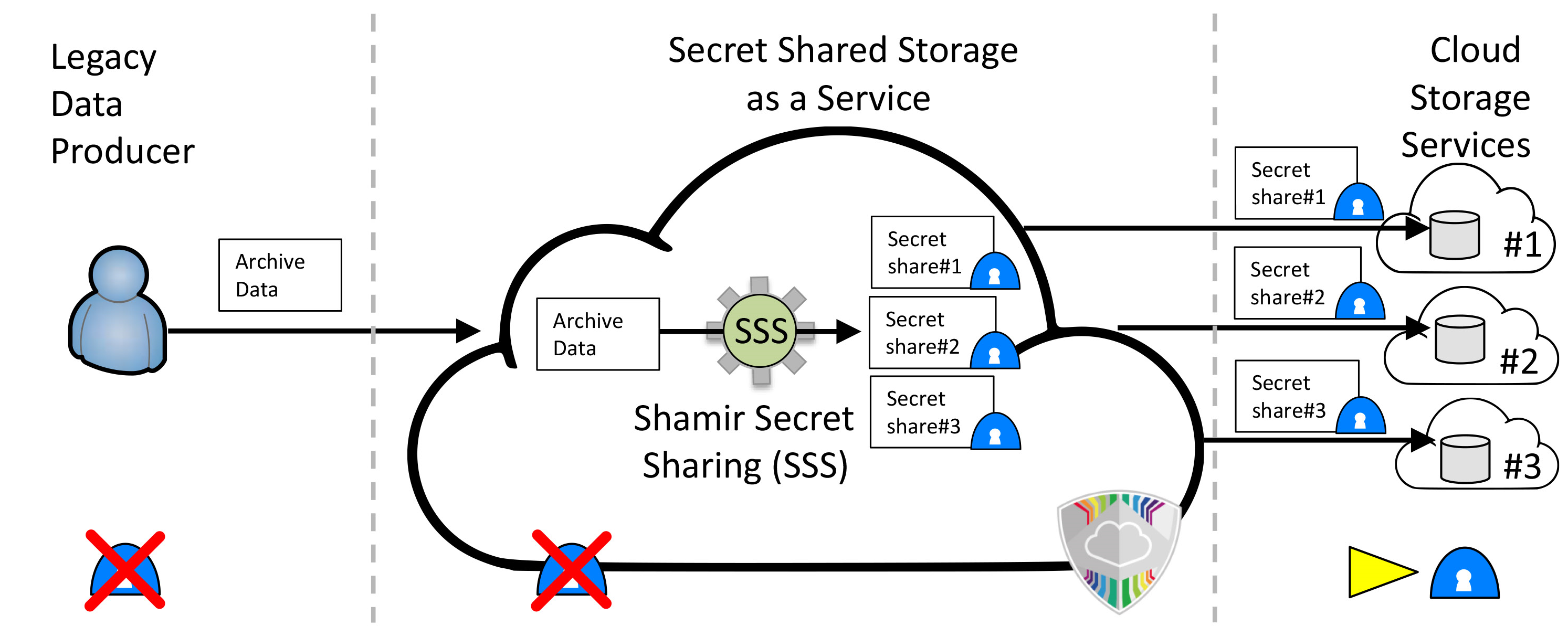 |
||
| Figure SAaaS: Files get split into multiple parts on the users’ device. The parts get sent to multiple cloud service providers. As with SAaaS, the availability can be increased if not all parts of the data are needed for reconstruction and the cloud service provider no longer has to be trusted w.r.t. confidentiality. |
Data Sharing Service (DSaaS)
The PRISMACLOUD data sharing service allows multiple parties to securely store data in a cloud-of-clouds network such that no single storage node learns plaintext data, while still enabling the owner to share the data with other users of the system, i.e., the data sharing service supports secure collaboration without the need to trust one single storage provider. The delivery model of this service is IaaS.
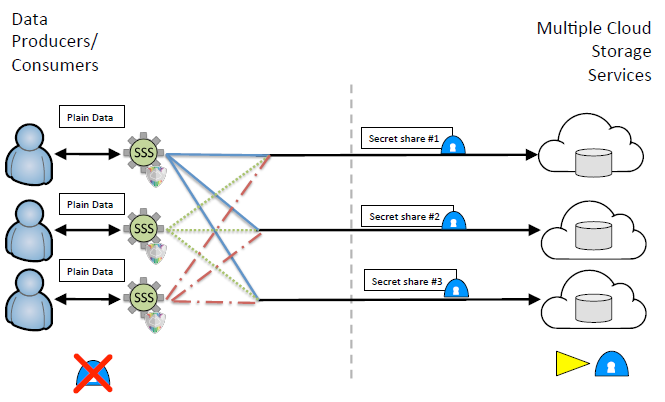 |
||
| Figure DSaaS: Files selected for archiving get split and then distributed to multiple cloud service providers. The user no longer has to trust the cloud service provider w.r.t. confidentiality. The availability of the data can be increased if not all parts of the data are needed for reconstruction. The proxy nature of the service allows legacy applications to use SAaaS. |
Selective Authentic Exchange Service
This service enables users to move their authentic documents to a cloud service and then delegate the selective sharing of parts of these documents to another party, while maintaining the authenticity of the selected parts. The other party can then verify the authenticity of the received data. The delivery model of this service is PaaS.
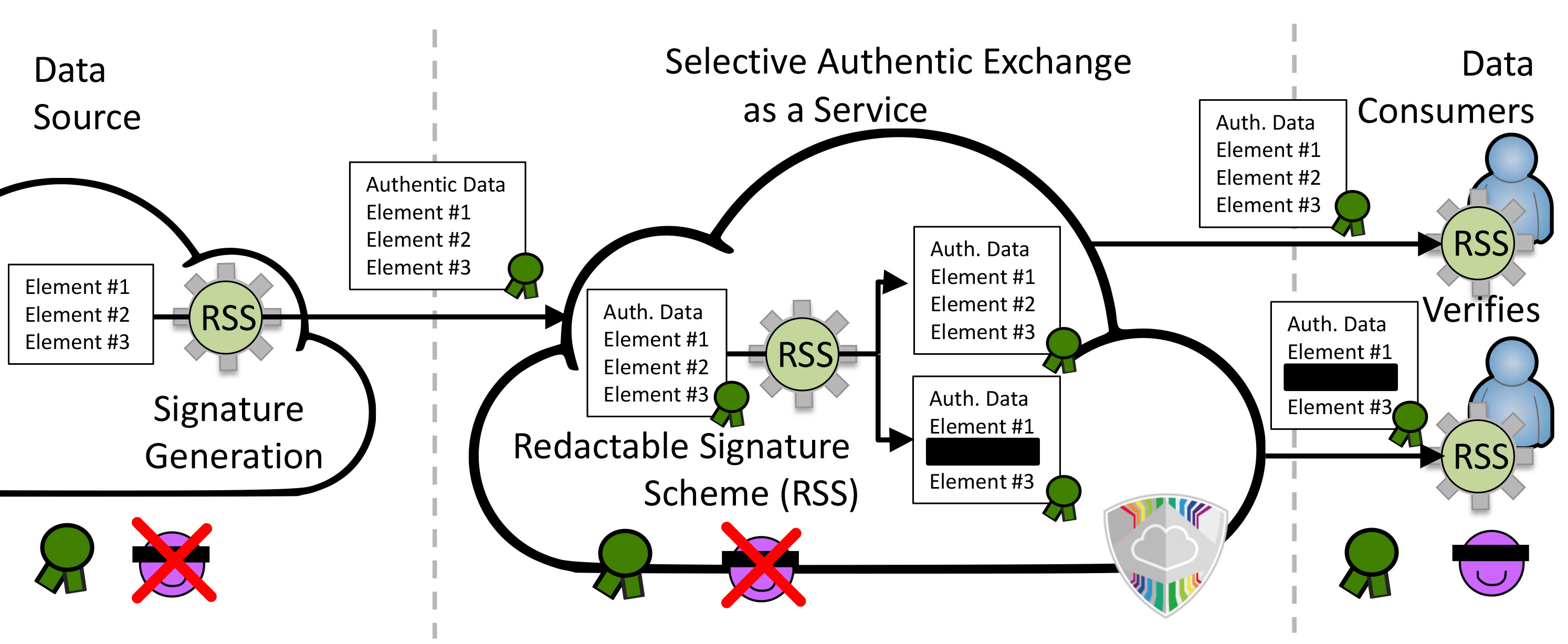 |
||
| Figure: Documents which were uploaded to the service can be redacted without invalidating the original signature of the document. Allowing the user to redact signed documents allows them to only share necessary information without sharing too much. On the flipside, the data consumer can be sure that the data they received were based on a signed document. |
Privacy Enhancing ID Management Service
This service offers the capability of a privacy enhanced identity management. In particular, it allows users to store their attribute credentials obtained from some entity (e.g, a service provider or an authority) in this component and to realize a selective attribute disclosure functionality. The delivery model of this service is PaaS.
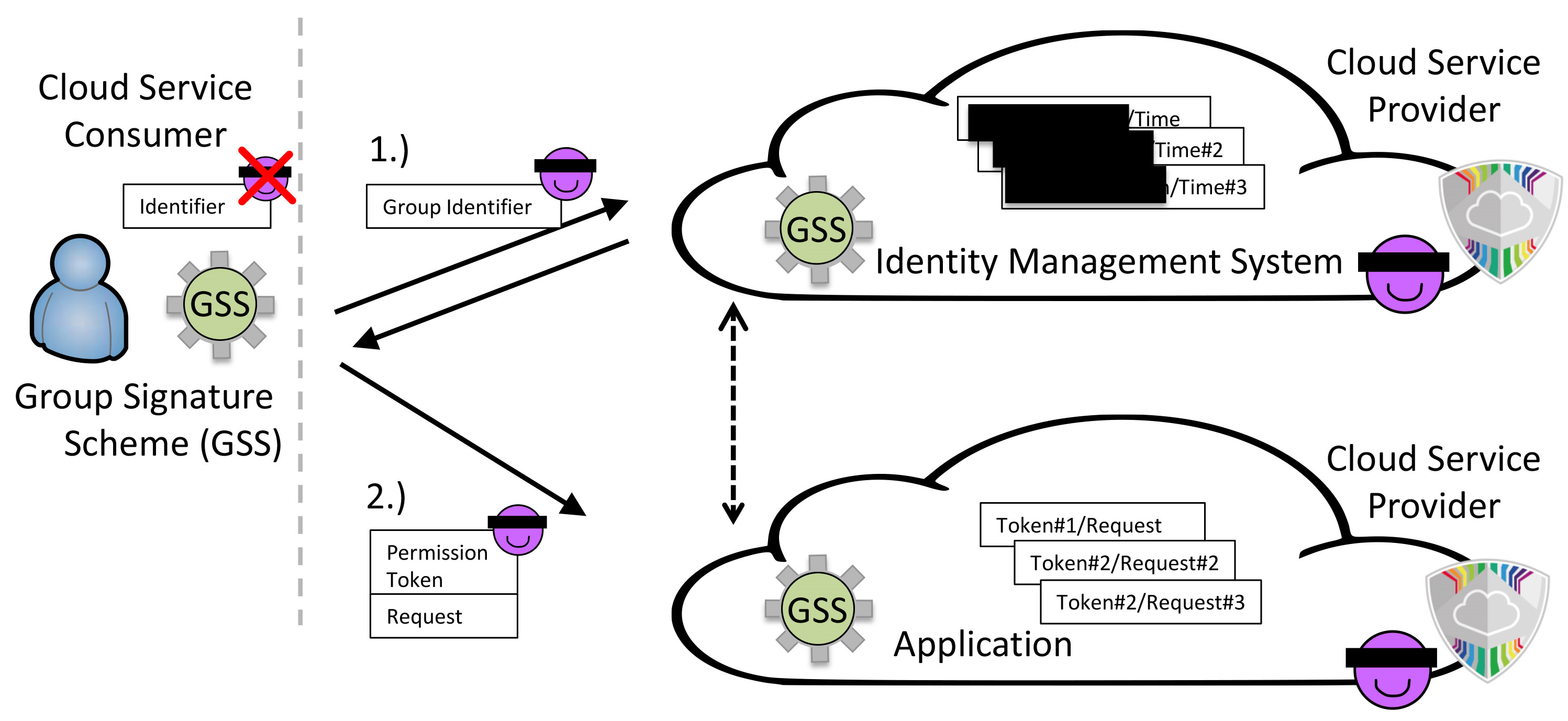 |
||
| Figure: Users are granted certain rights depending on the group they belong to. The service provider does not need to identify the users by ID to be sure they have the rights for certain actions. Increases trust of the user in privacy protection without impeding the service. |
Verifiable Statistics Service
This service provides the functionality to delegate the computation of verifiable statistics on authenticated data in a secure way. The computations have the feature of being public verifiability, i.e., any verifier can check whether an outsourced computation has been performed correctly, or not. The delivery model for this service is PaaS.
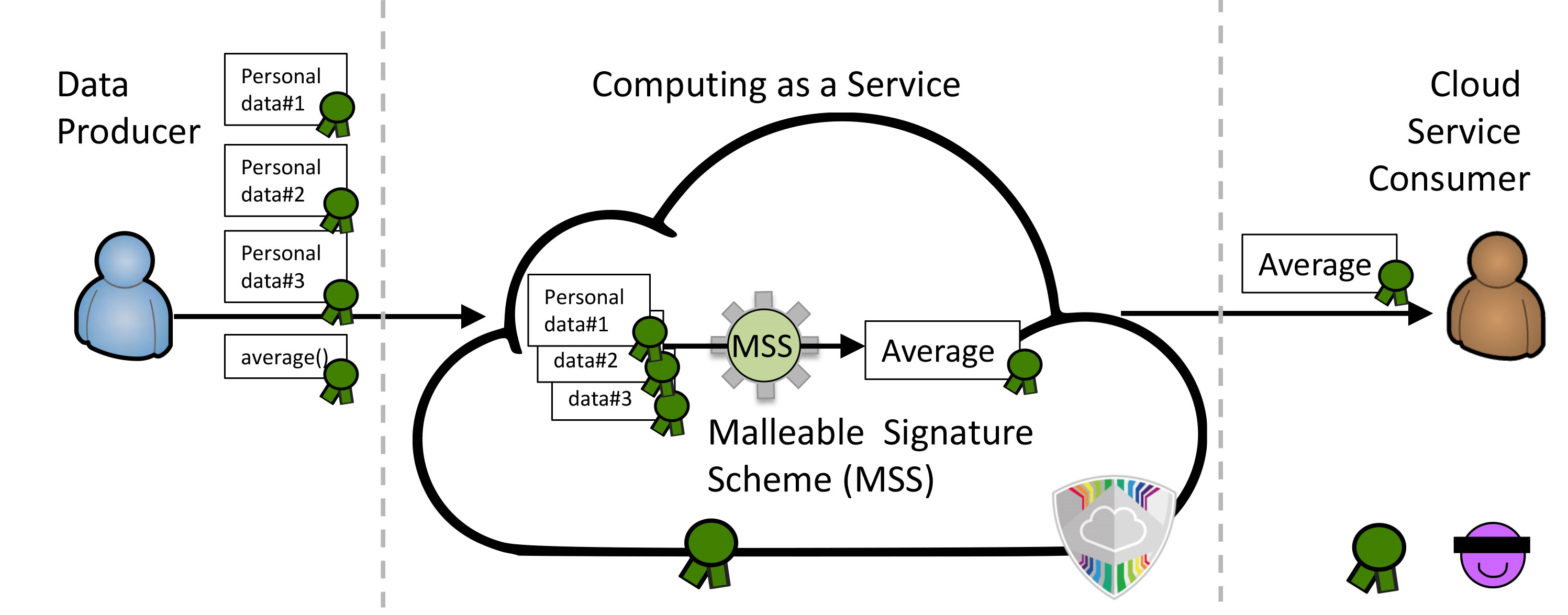 |
||
| Figure: The data producer sends signed data to the cloud. The cloud service consumer is then able to retrieve the result of a computation on the original data, which will still have a valid signature, thus proving the result was calculated using the input data. The cloud service consumer can validate their results without breaching the privacy of the data producer. |
Infrastructure Auditing Service
The infrastructure auditing service offers the capability to certify and prove properties of the topology of a cloud infrastructure without disclosing sensitive information about the actual infrastructure’s blueprint. The delivery model associated to this service is IaaS.
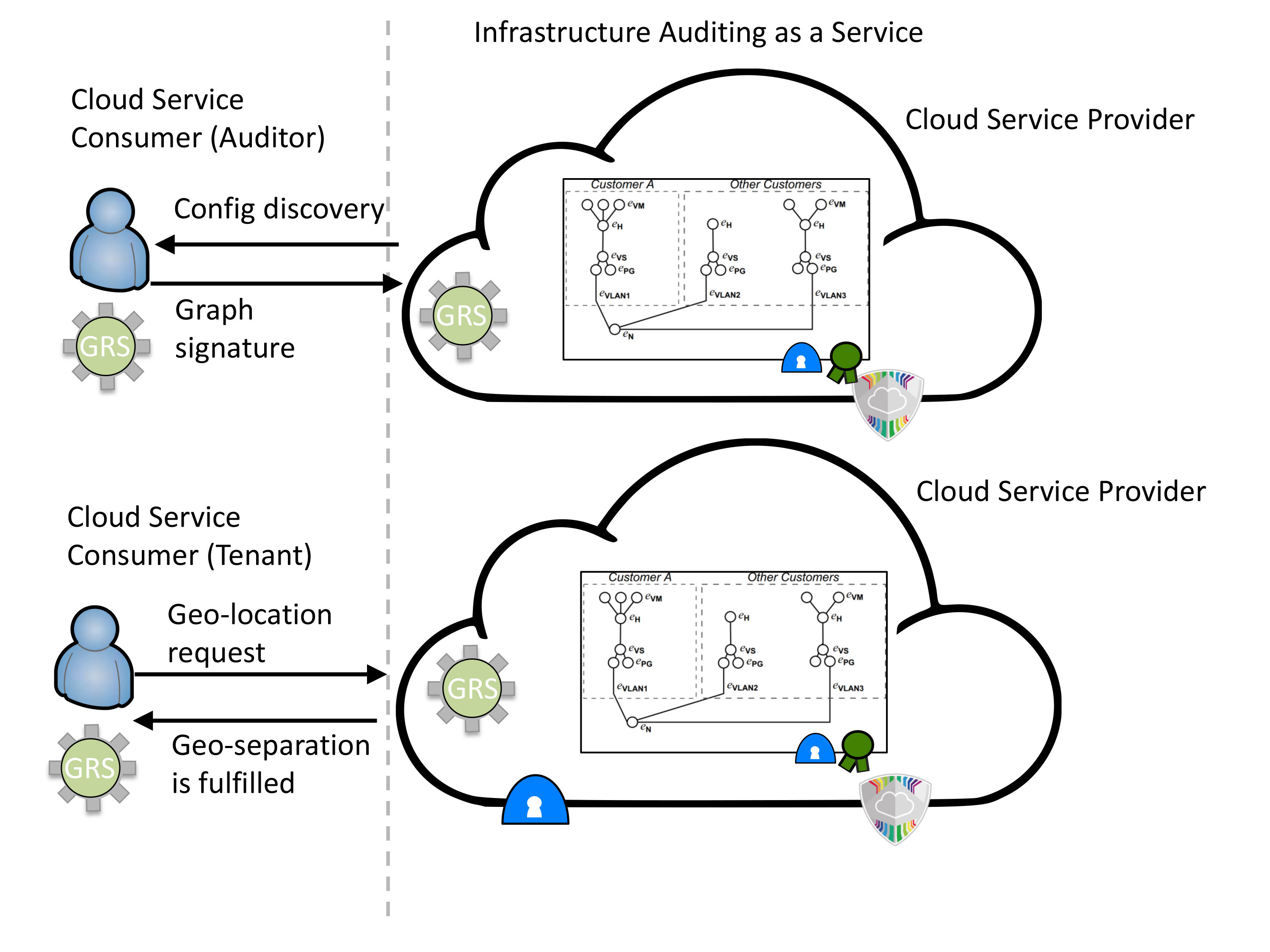 |
||
| Figure: An auditor creates a certifi cate based on a graph representation of the infrastructure of a cloud service provider. The cloud service consumer can then send a challenge request to the cloud service, which can only be fulfilled if the cloud service upholds the requirement. The cloud service provider no longer needs to grant access to their infrastructure in order to prove that they uphold the requirements. |
Encryption Proxy Service
The service supports moving legacy applications to the cloud by encrypting sensitive information identified within HTTP traffic in a format and/or order preserving way. The delivery model associated to this service is SaaS.
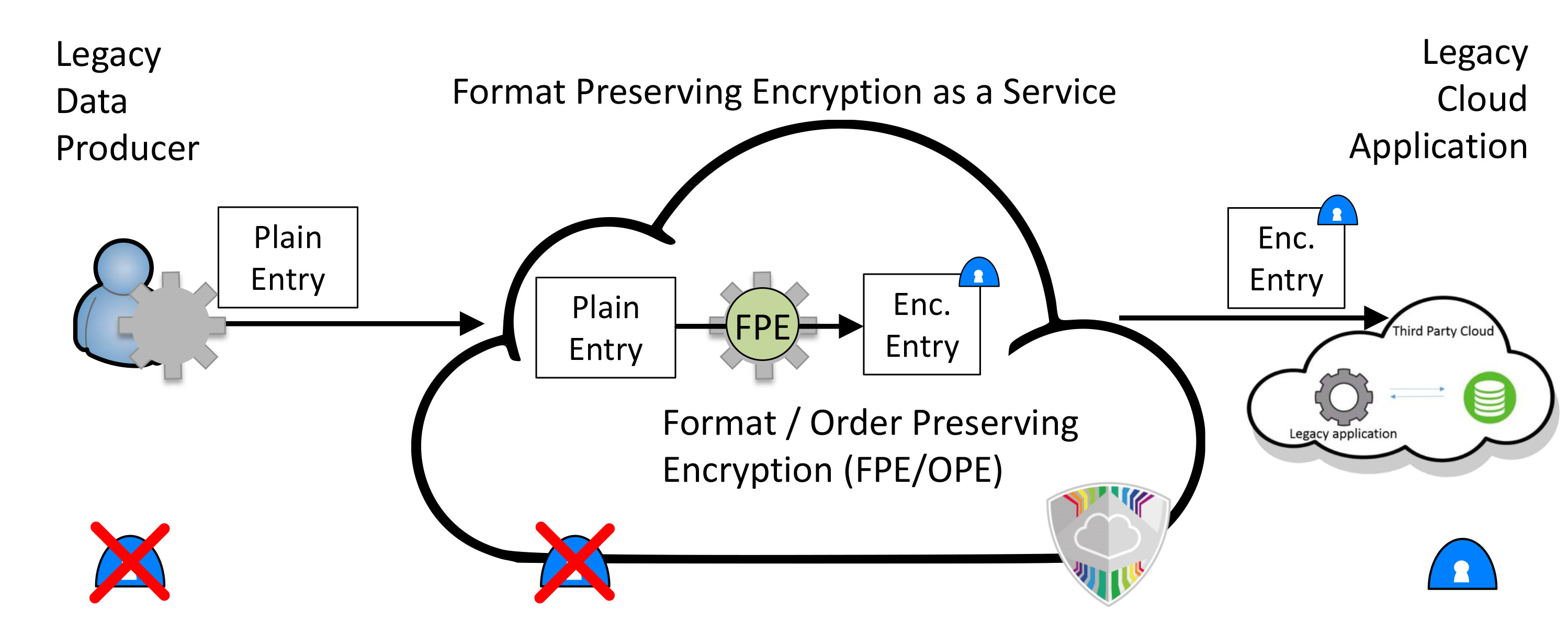 |
||
| Figure: The data producer sends unencrypted data to the encryption service, which encrypts the data in either an order or format preserving manner and then sends it to the cloud service provider. When requesting data from the proxy, the request is modifi ed by the proxy to work on the encrypted data, retrieves the requested data from the server and then sends the decrypted data to the cloud service consumer. |
Anonymization Service
This service enables users to anonymize large data sets, and in particular database tables. The service allows users to identify private and sensitive information in the data sets and produce an anonymized version of the data set. The delivery model associated to this service is SaaS.
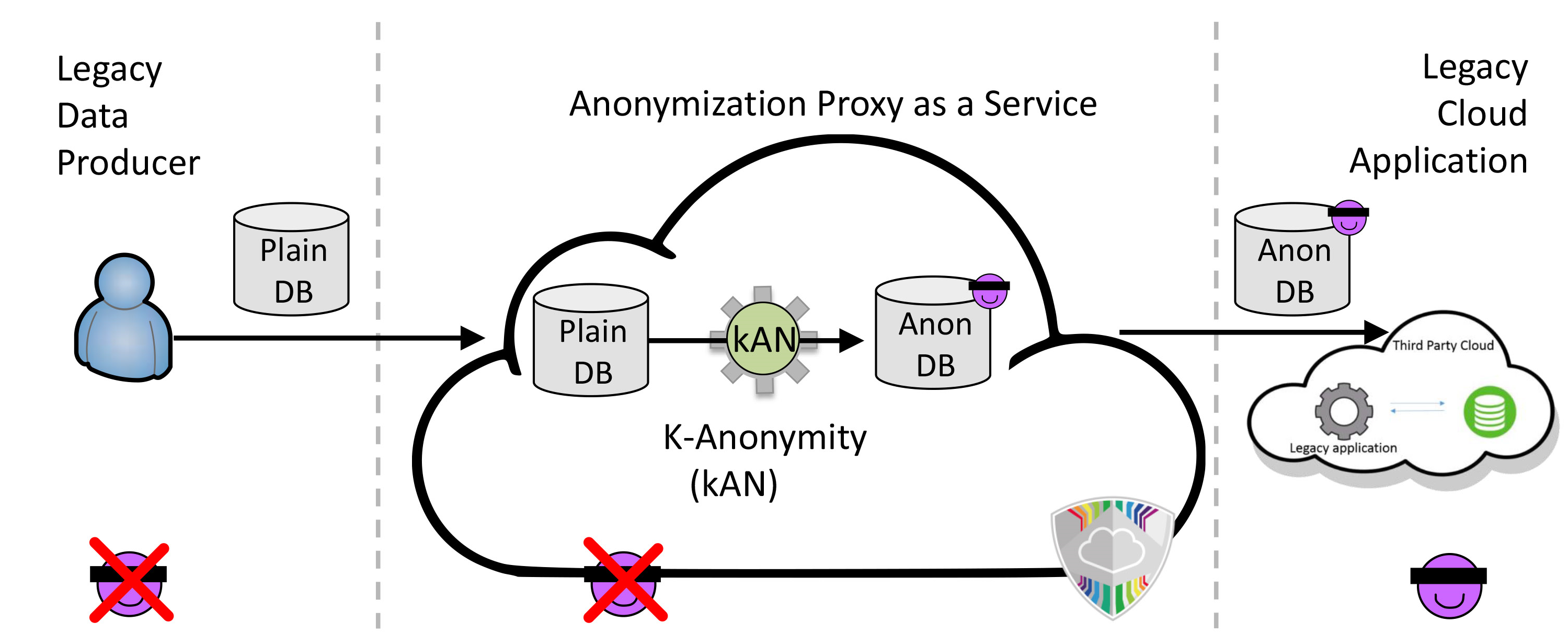 |
||
| Figure: Plain data stored in a legacy database is analyzed and is obscured enough so no connections between the datasets and the user can be made. The user’s privacy is protected while the cloud service consumer can still make calculations on the obscured data. |

