D3.4 Progress Report on Business and Governance Models for Cryptographically Secured Services
Contributing Partners
ETRA, ATOS, FCSR, IRT, LISPA, MPL, XiTrust, IBM
Executive Summary
The present document compiles the work carried out in T3.3 business and governance models after one year and a half of the start of the project.
It begins with a brief analysis of state of the art business models in the cloud computing with special focus on the challenges and opportunities brought by the use of crypto tools, being:
1. Security and privacy by design in cloud services
2. Authenticity and verifiability of data and infrastructure use
3. Confidentiality, integrity and availability for data at rest
4. Development of a methodology for secure service composition
5. Cloud Standardisation gap
Then, we make an analysis of the business models that could arise in the demonstrators of the project by the use of the PRISMACLOUD toolbox. Four steps must be carried out for the complete analysis, as depicted in the figure below. This deliverable covers the first three steps:
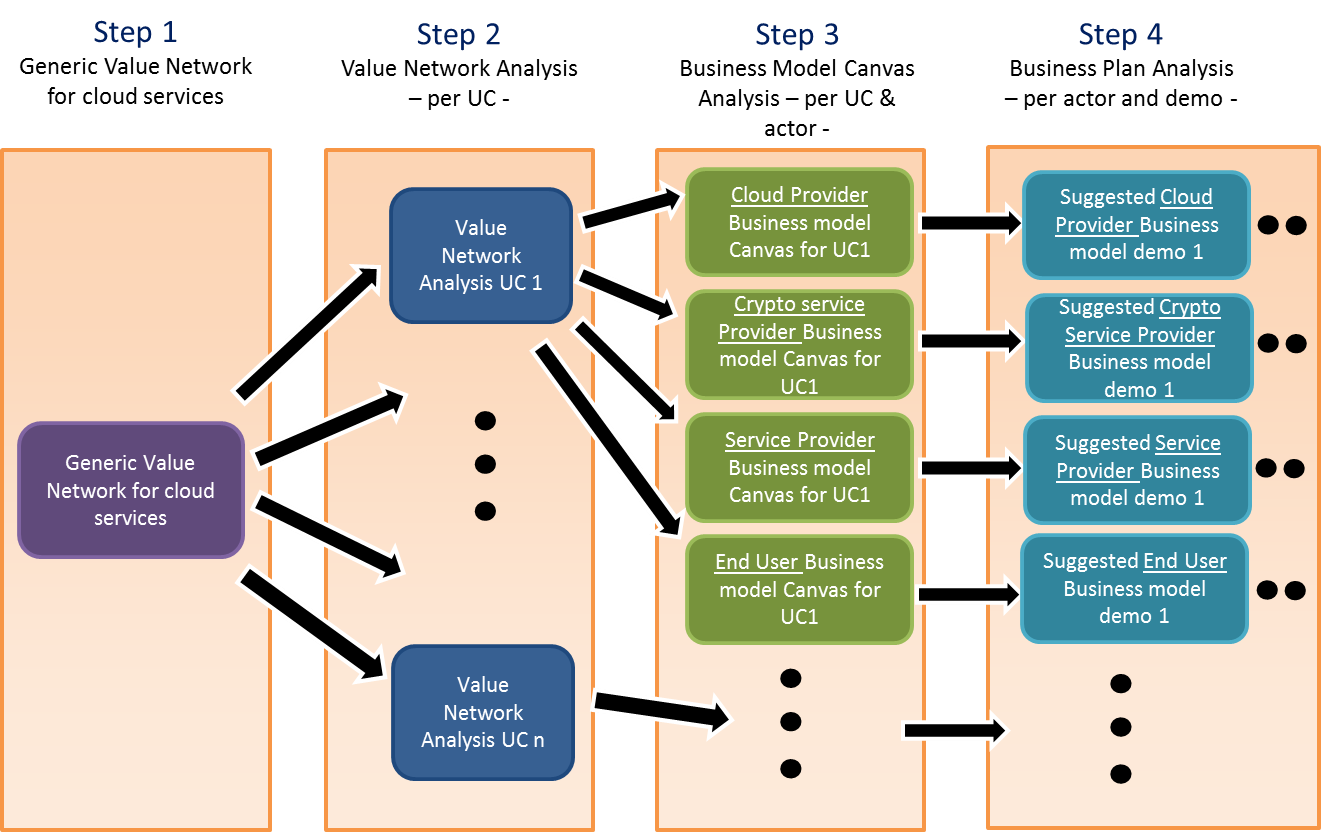
Figure 1: Overall methodology for analysing business models
The starting point for bulding business models is the generic value network for cloud services defined in [1], which describes the main contributions by all involved business actors for a certain product/service to be delivered to its current and prospective customers. Value network analysis is considered to be well-suited for understanding the exchange of goods, money and information flows in Internet-based ecosystems:
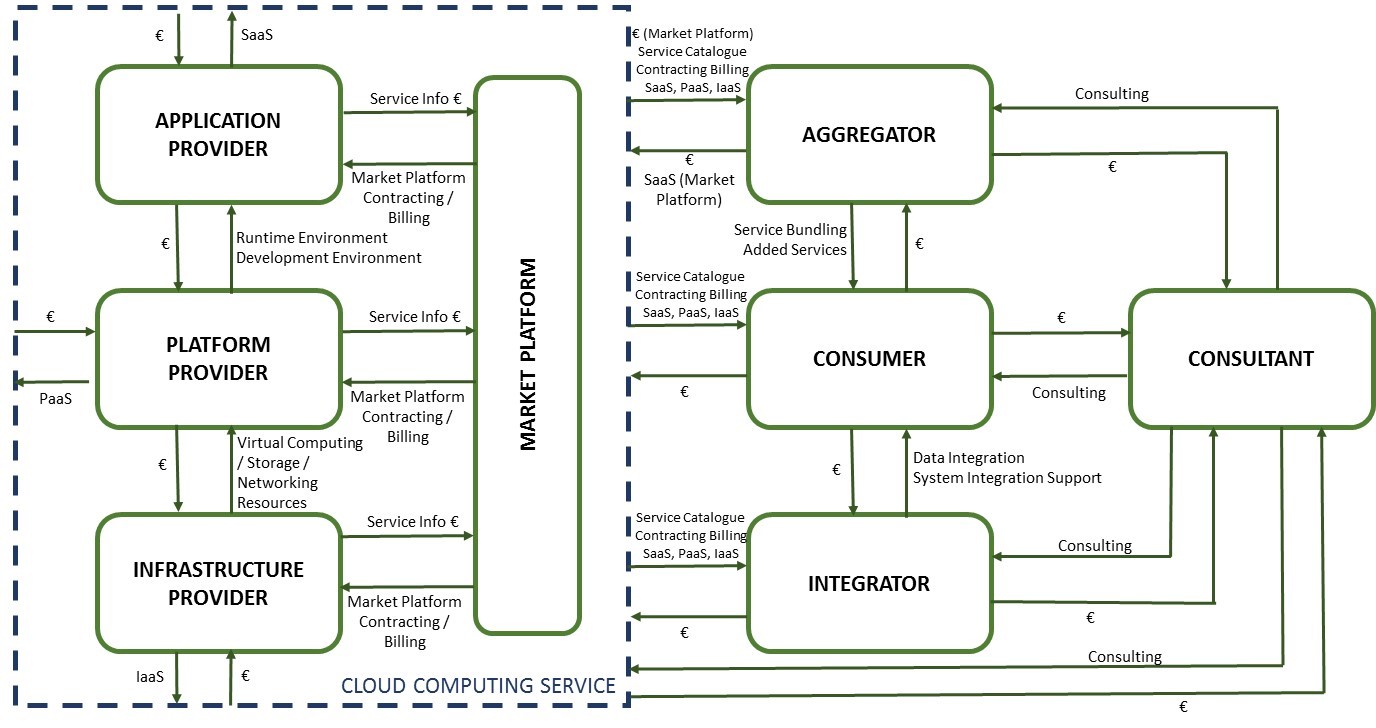
Then a total of seven use cases are detailed with a complete business analysis identifying roles, actors, value proposition, revenue streams, cost streams and other relevant indicators. After that, the Value network analysis is created for each one of them.
A Business model canvas is filled in in each of the areas of the project: Smart Cities, eHealth and eGovernment to better describe and design the business model.
Finally the latest section gives hints on what the future work will be in the task, and it will be reported in the deliverable D3.5 Business and governance models for cryptographically secured services.
